Network Access Control
Realtime NAC detects security threats on endpoints in real timeFully secure wired and wireless endpoints
Tgate is a Network Access Control system that checks the security condition of all the wire and wireless endpoints that have access to the network in order to protect company network the and all endpoints completely.
Wired and wireless devcie management
IP management
User authentication
Integrity check
Overview
Persistent internal security incidents
Since the 03.20 network attack situations on both South Korea and Bank-N, which were caused by uncontrolled endpoints, ground-breaking solution is in demand. In order to prevent such security accidents in advance, an introduction of NAC(Network Access Control) system can be established. This allows strong main control.
Tgate allows implementation of good anti-virus program to all company PC's in a shortest amount of time.

NAC with strong control
-
Solution 1
Gate in the wall
Tgate is a solution where all the connected devices can be controlled according to main security policy, and only approved and quarantined device may have internal access.This technology has logical network separation to keep the company's internal network safe from external network that work likes a buffer zone. The result is strong protection of internal network from unapproved user or devices.

-
Solution 2
real-time NAC
Tgate real-time *NAC interlocks endpoint security threats to a network security equipment to detect and block threats in real-time. Integrated control is not an individual management, but an effective and powerful system built to operate security management through real-time policy to be in compliance to numerous security related legislations including personal information protection act, copyright protection act. Real-time NAC should be mandatory, not an option.
* NAC : Network Access Control
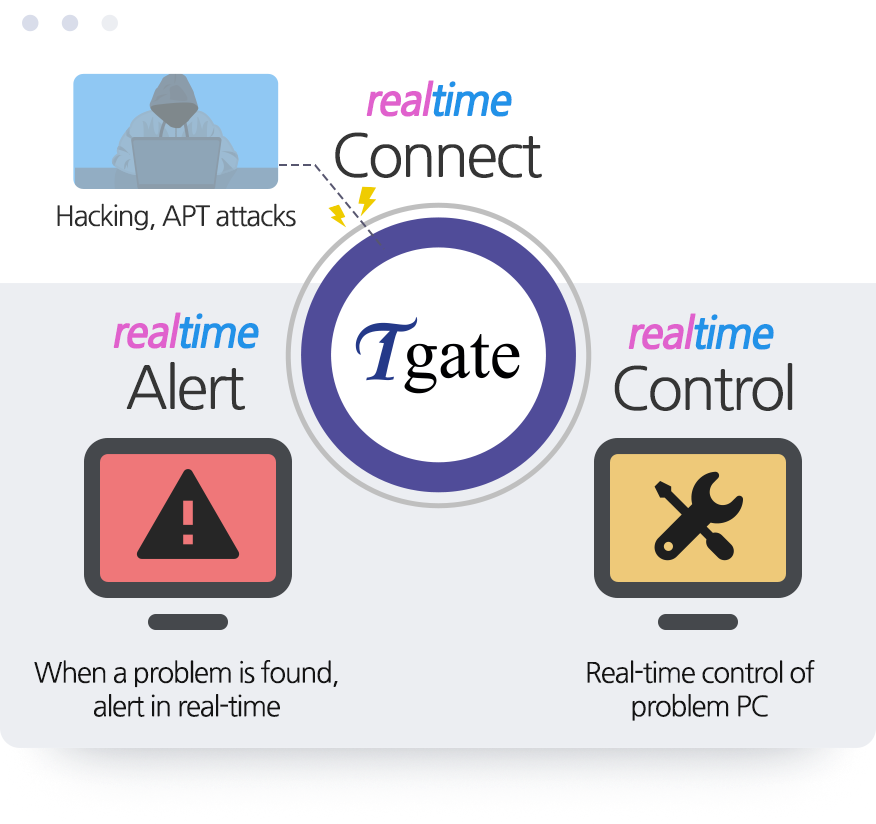
Logical configuration of endpoint internal security
-
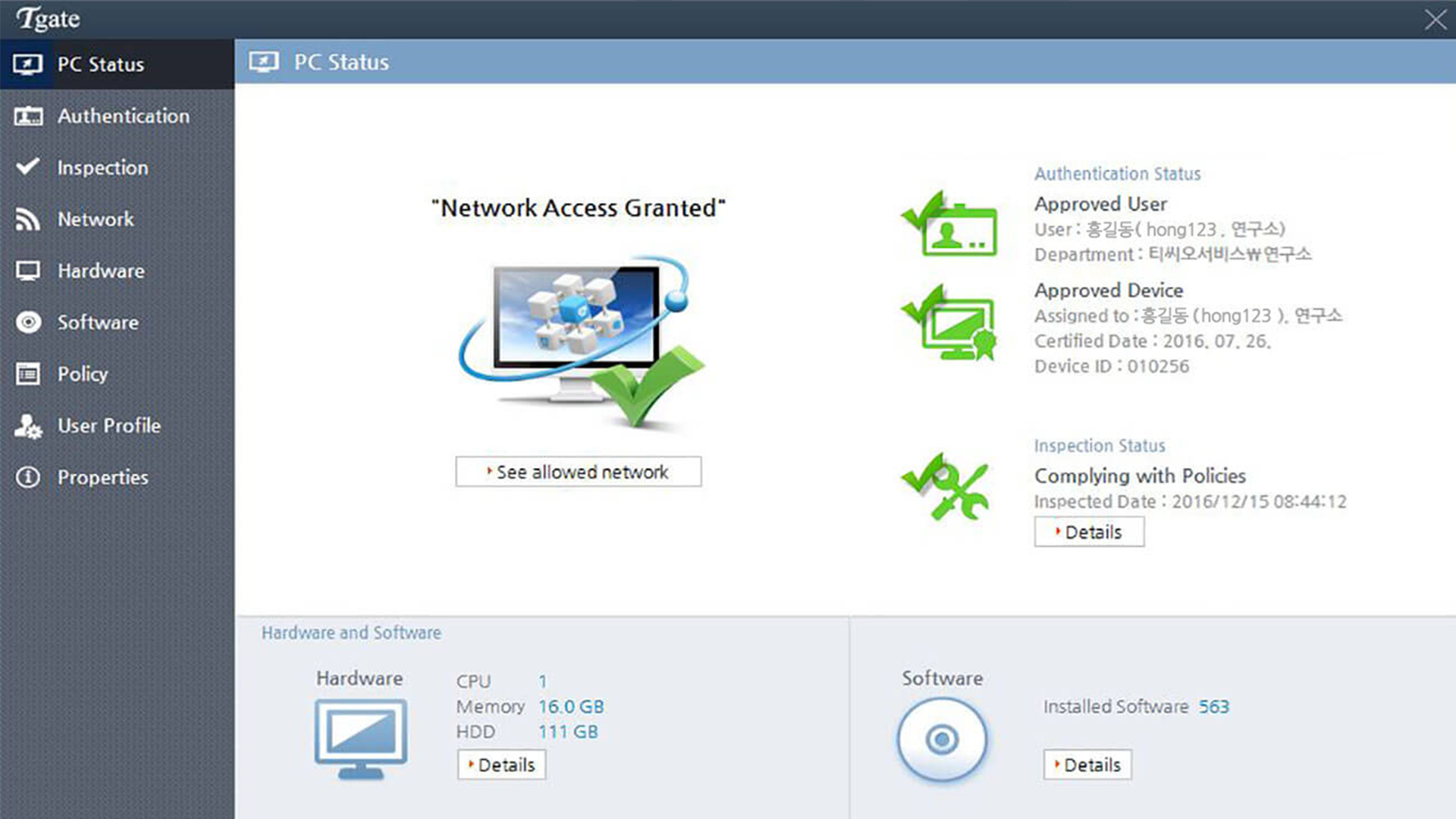
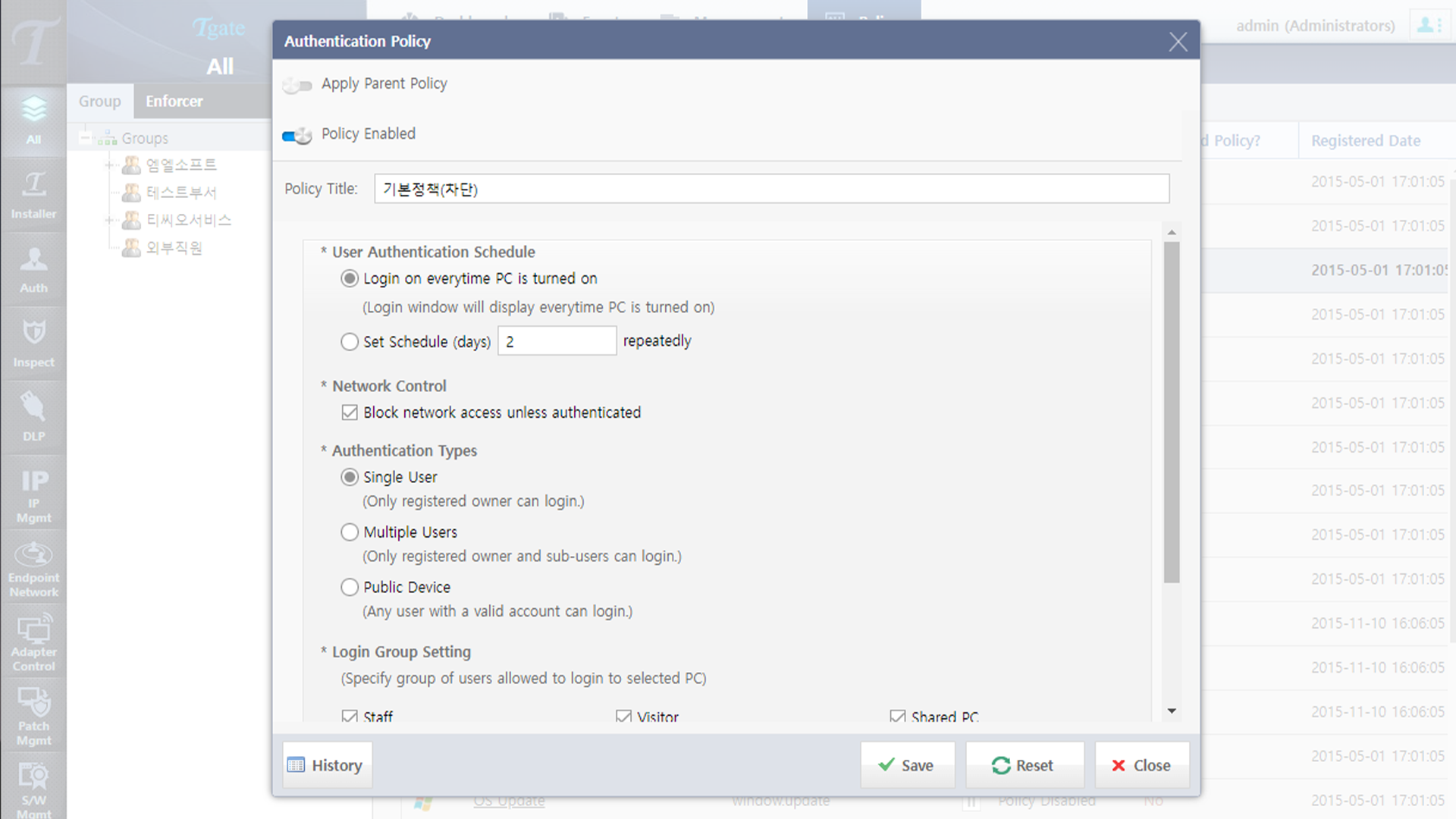
01. Authentication
Tgate minimizes the possibility of network access by unauthorized persons by providing identification and control for users by combining the user's ID/PW, IP, MAC address, and device authentication key.
-
02. Quarantine
Even if authenticated, only endpoint devices that have passed the integrity policy can access the network.
-
03. Authorization
Provides a secure internal network operating environment by classifying internal network access and authorized users to grant and control privileges according to policies.
-
04. Privilege
Even after users access the network, the integrity of the network and endpoints is always maintained through continuous management and monitoring.
-
05. Audit
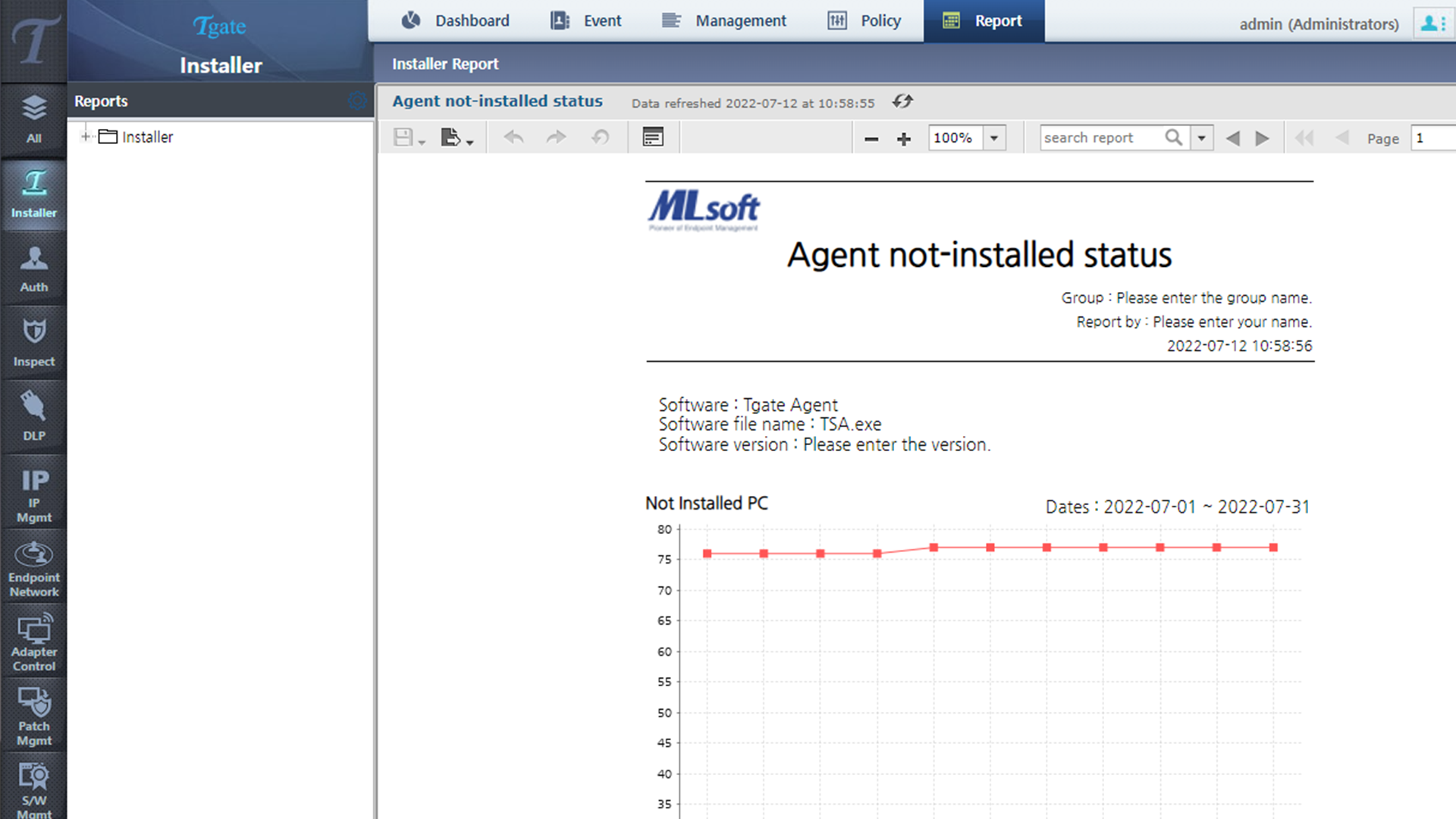
The status of the in-house system is written as a report, so statistics can be easily identified and used as a report.
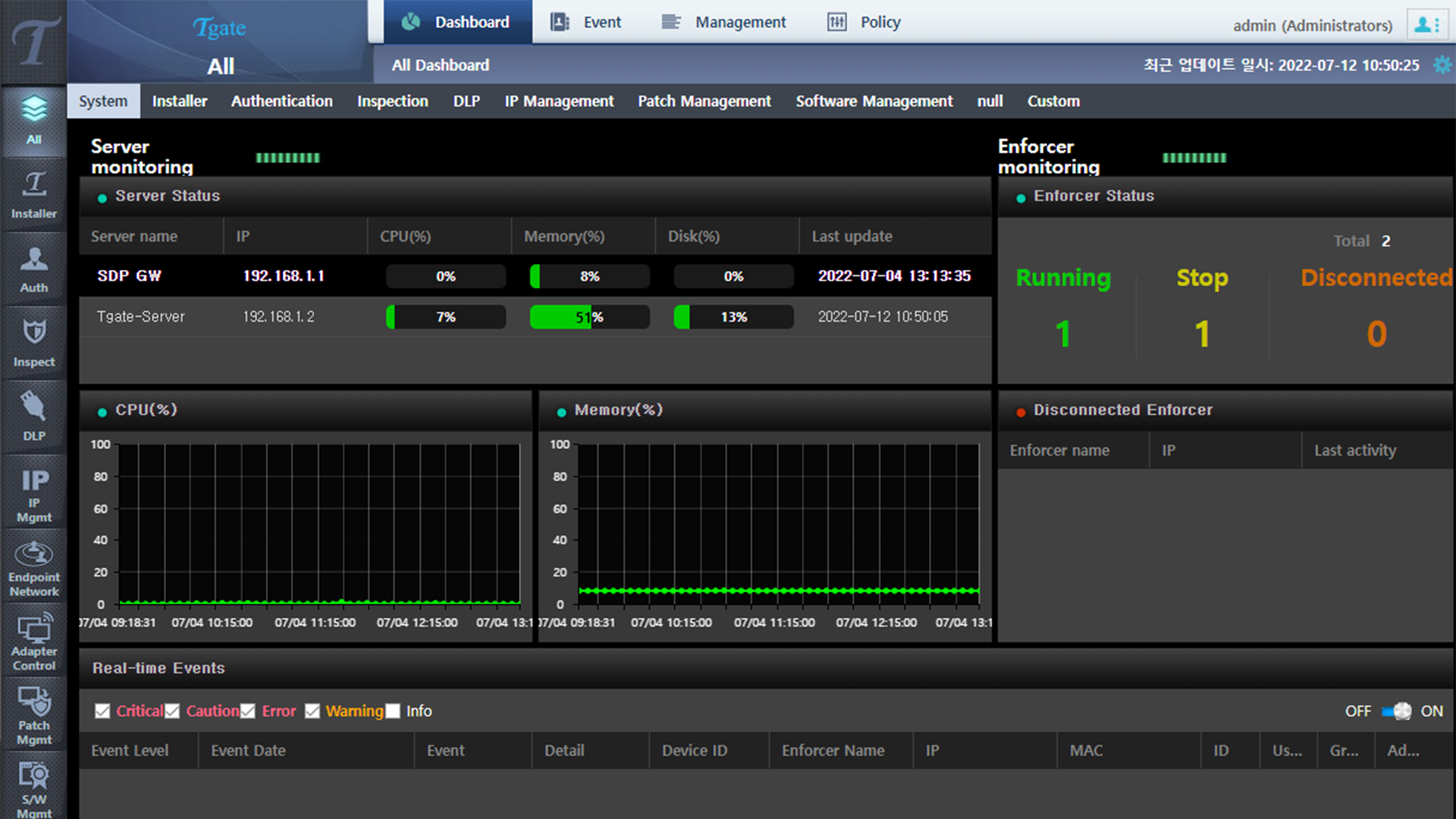
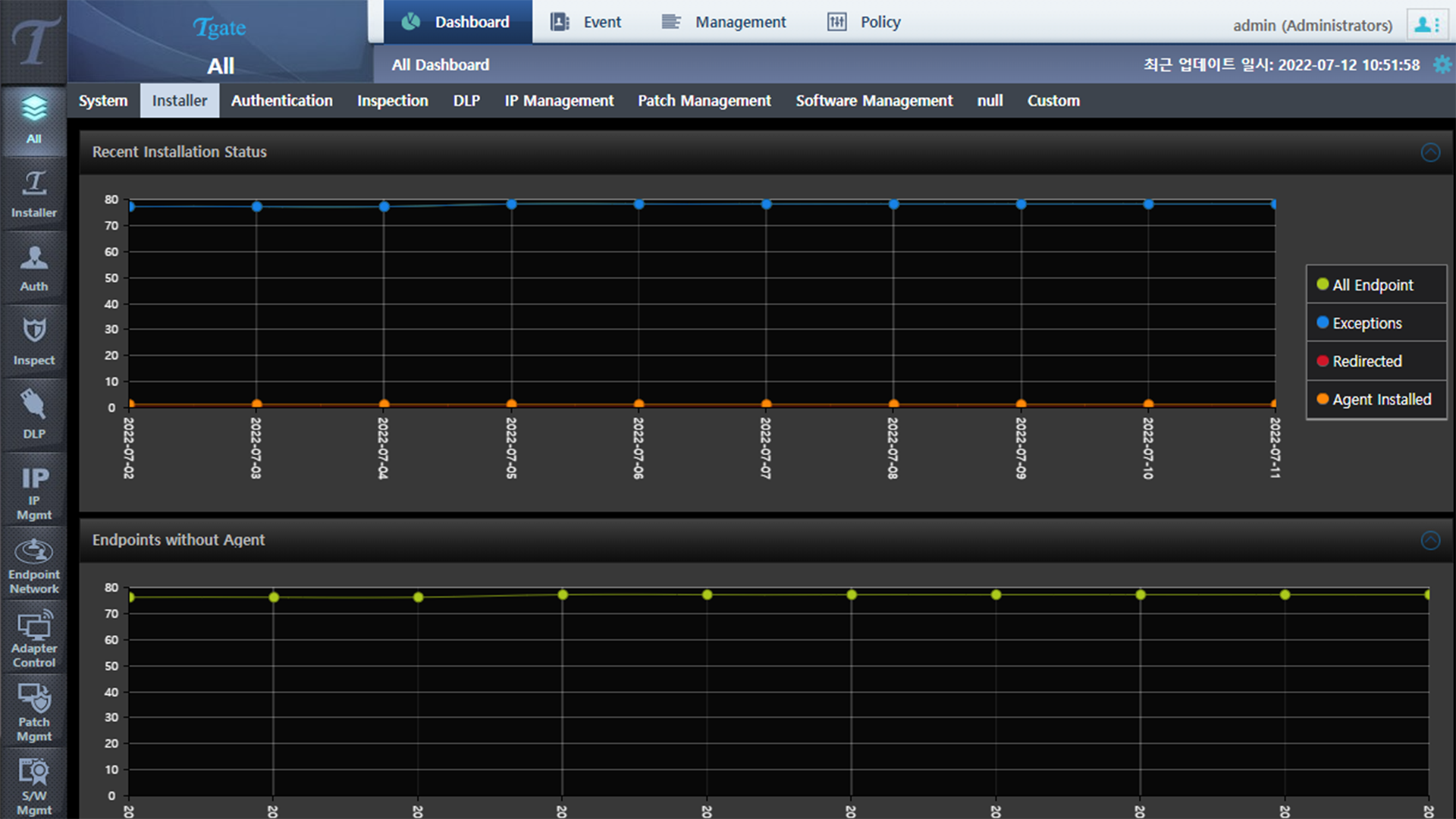
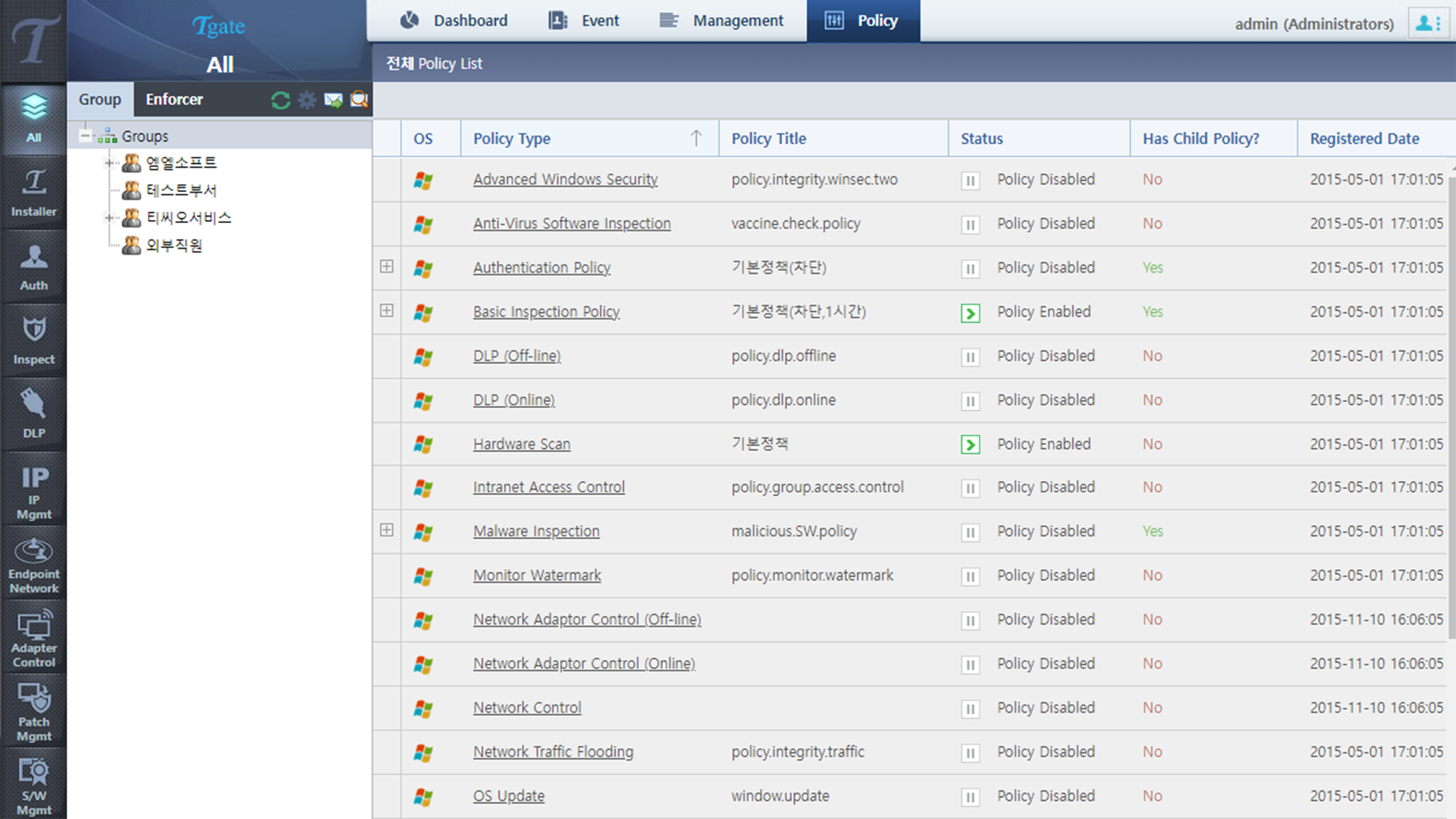
Screenshots
Main Features
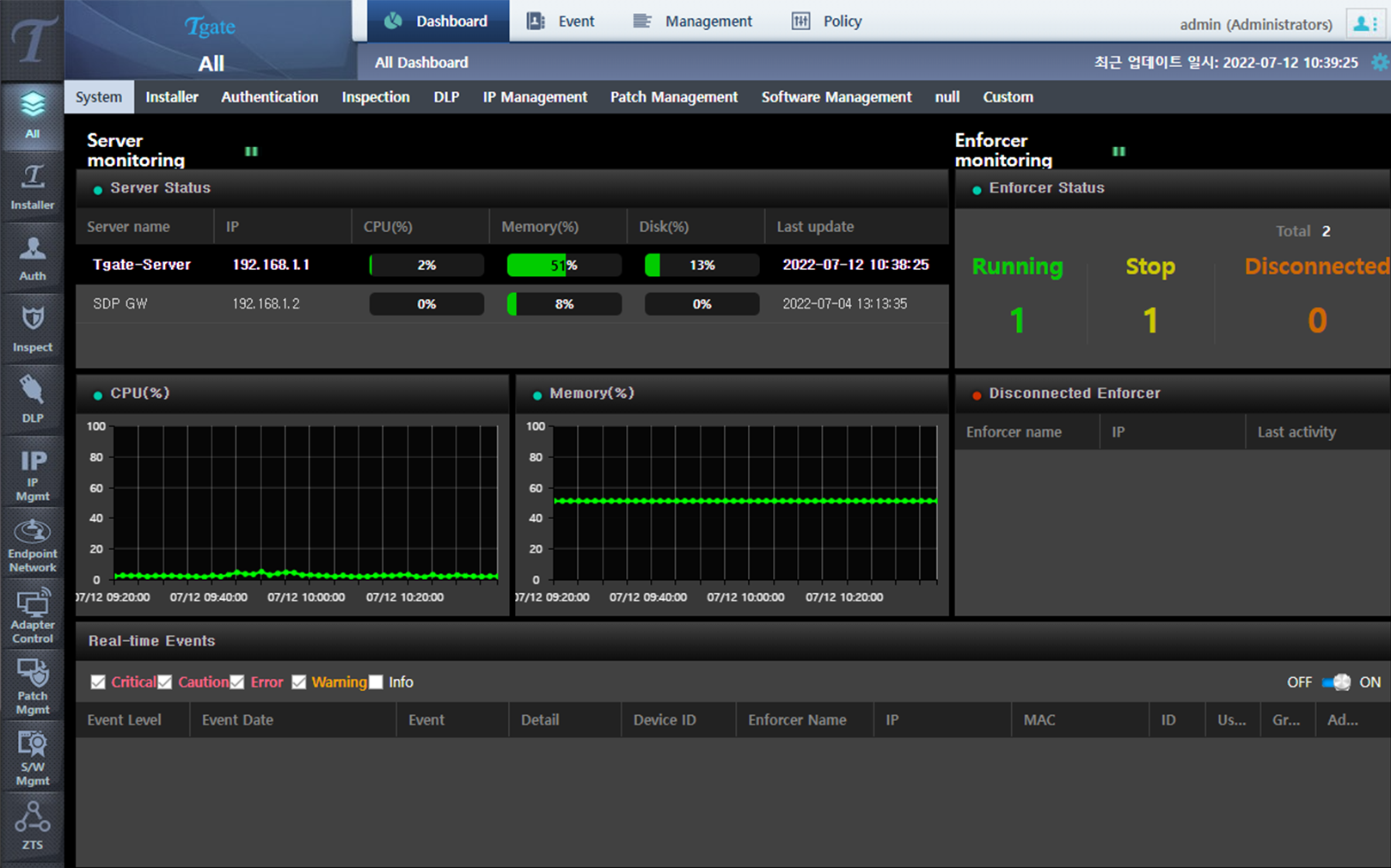
Real-time terminal control
- Real-time terminal user identification
- Real-time terminal log monitoring
- Real-time threat detection response
- Real-time terminal log threat search
- Real-time PC based traffic block
- Real-time network based control
Automatic terminal information collection
- Real-time IP/Mac detection
- Terminal endpoint detection
- Terminal On/Off status detection
- Hardware information collection
- Software information collection
- Terminal Operating system detection
IP management
- IP user mapping (IP real name)
- IP collision protection
- Fixed DHCP server
- IP traceability
- IP enabled application/system approval
User authentication
- PC based authentication agent
- Web based authentication screen
- Interlocks Active Directory, LDAP, SSO, and other authentication
- Existing personnel DB linkage
- Detect and authenticate all endpoints
Software integrity check
- Network control for failed sofware integrity check
- Mandatory Software Inspection inspection
- Malicious software installation inspection
- Latest patch compliance inspection
- Illegal software installation inspection
- Vaccine sofware instllation inspection
Optional Features
PC Advanced Security
- Enforce automatic OS update
- Enforce Windows Firewall settings
- Remove trash
- Remove Security tab of a file / folder
- More than 30 OS control functions
Terminal network management
- Block Tethering
- Block unlicensed Wireless AP
- Block bluetooth, T-login, Wibro connection
- Gather open port terminal information
- Group network access control
Device use restriction
- Monitor/Block USB port
- Monitor/Block CD-ROM
- Monitor/Block network drive
- More than 10 communication function
Privacy protection
- Personal information inspection
- Specific file inspection
- User custom pattern inspection
- Encrypt detected personal information file
Strengths
Leading companies' choice

To effectively operate Network Access Control 'NAC', IP Management System 'IPMS' collects applicable subject, Cental PC Management System 'DMS' maintains integrity and manages security condition, and Patch Management System 'PMS' is needed. All these system interlocks to control and manage endpoints effectively. Tgate provides strong control and efficient management of your endpoints with these technologies.
Benefits
Management / Operation
- Enforce mandatory user's software
- Increase user convenience with integrated account management
- Increase user required software update management
- Illegal software management and advance control management
- Simplify time to analyze cause of terminal failure
Related laws / Guidelines
- Information leakage prevention law - Prevention of information leakage
- Personal Information Protection Act - Personal Information Management
- Copyright Protection Act - Illegal software use control
- IMS Certification - EndPoint Management
- IP Real Name Contribution - Management of all devices where IP exists
Security
- Required software Must be used to increase security and enhance
- Enhanced user management with user integrated account management
- Malicious code pre-control with illegal software usage control
- Prevention of large security accidents
- Security Regulatory Compliance and Supervisor IT Security
Maintenance
- Centralized management ensures quick response to the cause of failure
- Updating and Maintaining End Point Solutions
- System integration of existing management system
- Reduced redundant operation cost by linking with asset management, IP management, NAC, etc.
- Consolidated system reduces individual unit security product requirements
Configuration

Operating environment
| Division | Supported environment |
|---|---|
| Policy Server | Redhat affiliation Linux OS |
| Console | Chrome, Edge, Firefox |
| Enforcer | Appliance Equipment, TCP/IP Network Environment |
| PC Agent | Windows OS |