Safe and free network
Tgate SDP is an Open Network security solution designed around user identity to improve the limitations of the existing network-centric security.
Protect IP information
DDoS Attack Prevention
Identity-based access
Dynamic Firewall
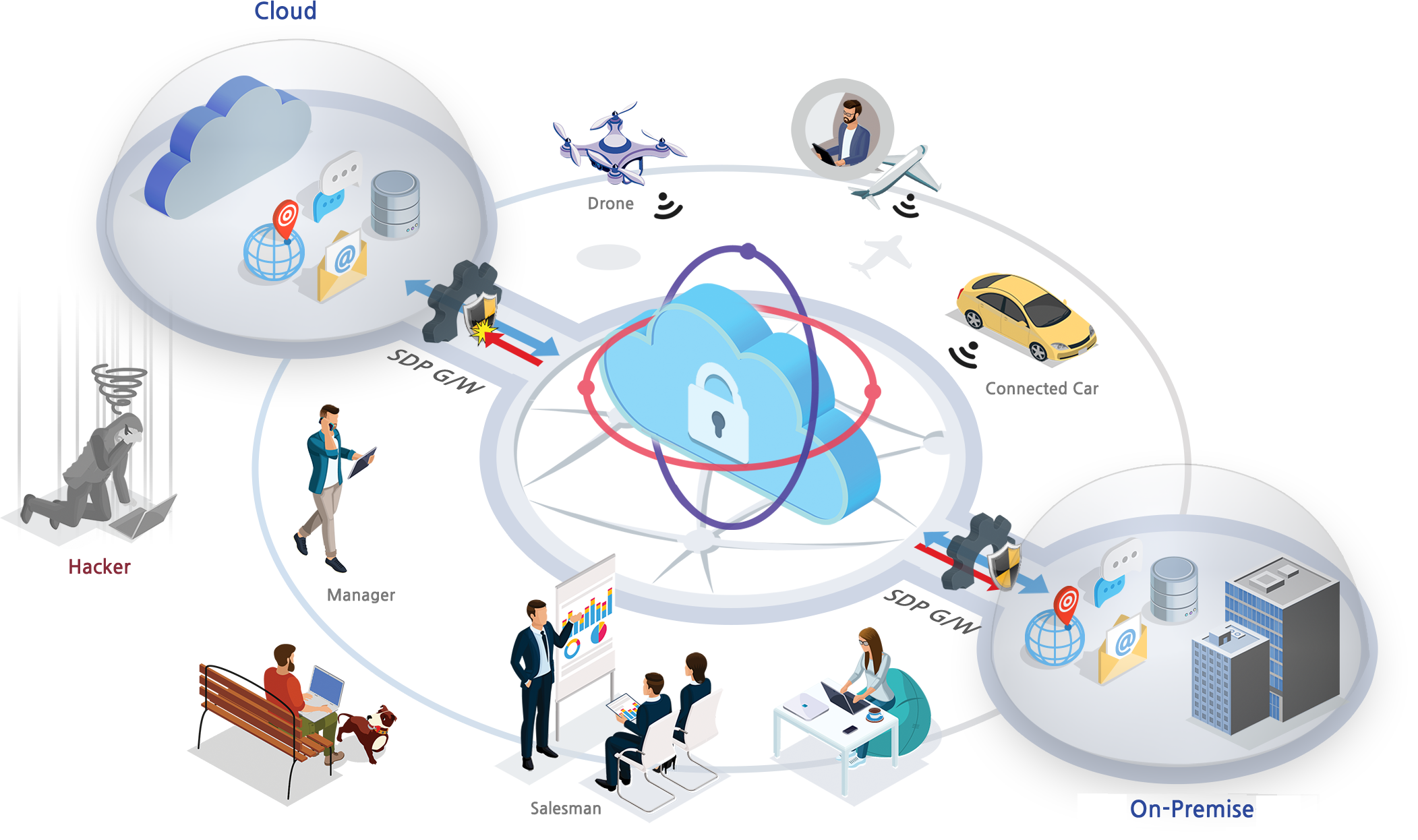
Overview
Business is getting wider
In the 5G era, information can be produced and collected not only from PCs but also from various terminals such as IoT. Now, it is rapidly changing from a closed in-house computer system to an Open Cloud System so that work can be viewed from outside. However, due to this, security threats are increasing, and there are many insufficient parts to prepare for the cloud environment with the existing network-based security solution centered on the internal network.
Tgate SDP dramatically improves work restrictions due to space limitations so that access to the closed internal network is no longer required.

SDP with extensive network control
-
Solution 1
SDP
SDP is an abbreviation of 'Software Defined Perimeter', and it connects secure communications safely outside the company while controlling applications that match the privileges granted to the user. In the black cloud-based SDP, users no longer need to access only the closed internal network, which will remove the spatial constraints of the business.

-
Solution 2
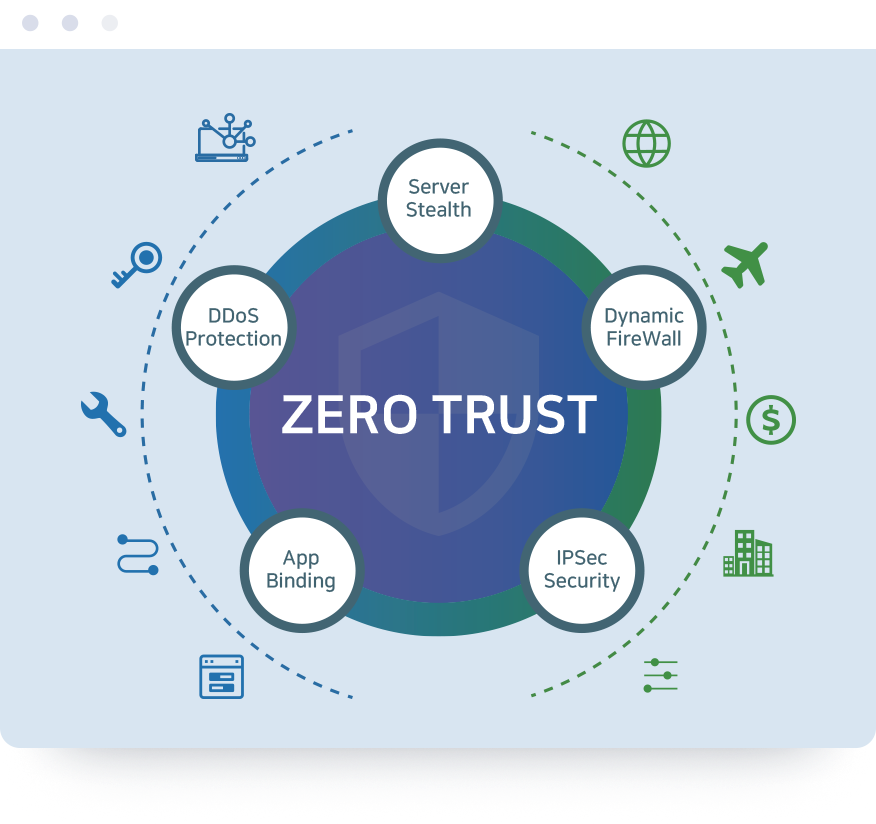
Zero Trust
The Zero Trust Network has a security theory that requires re-identification to access the system under the premise that 'everywhere is at risk and no one should be trusted without proper authentication,' regardless of whether it is inside or outside the company. Along with strong security, it simplifies deployment without disrupting the user experience.
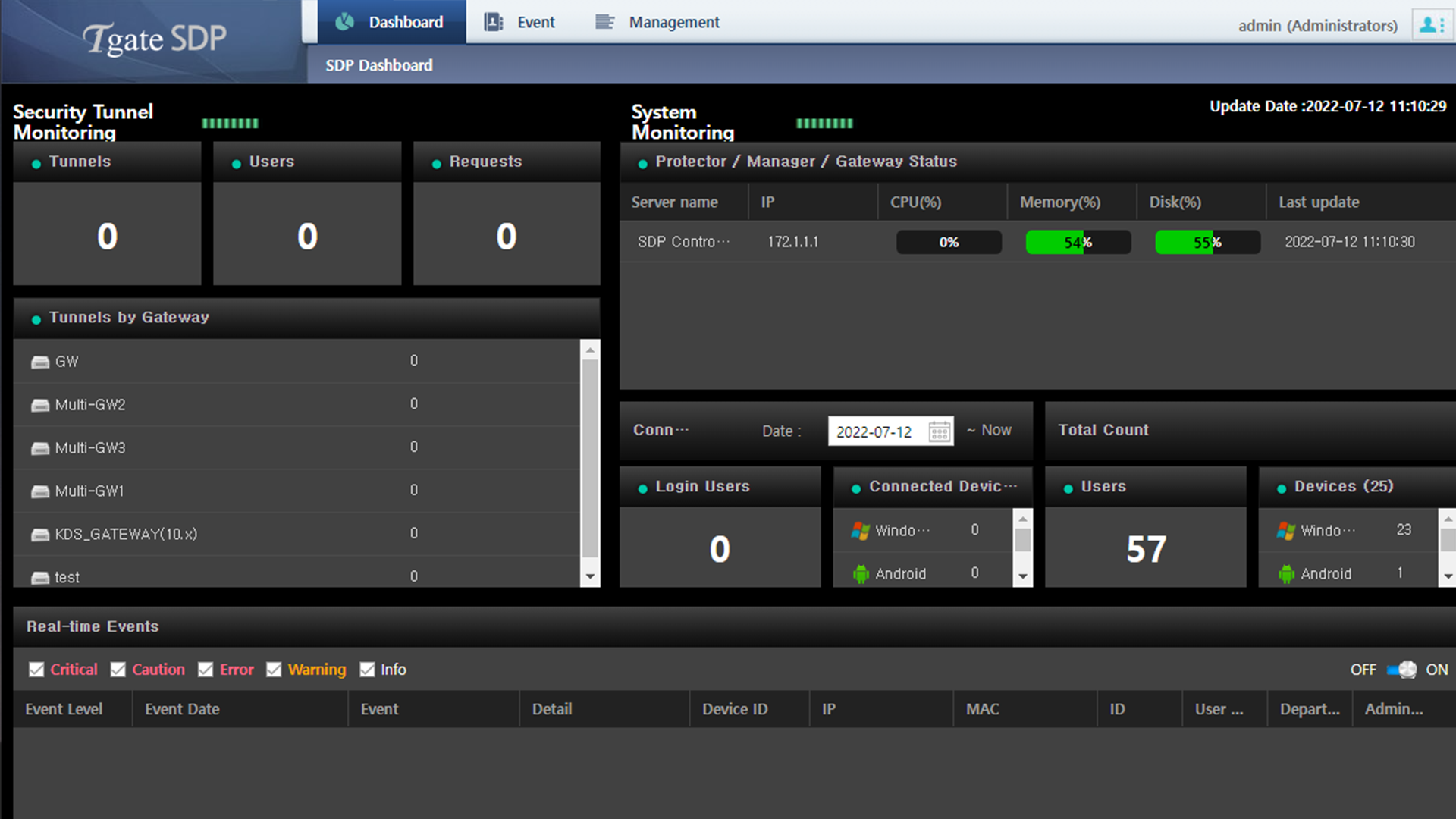
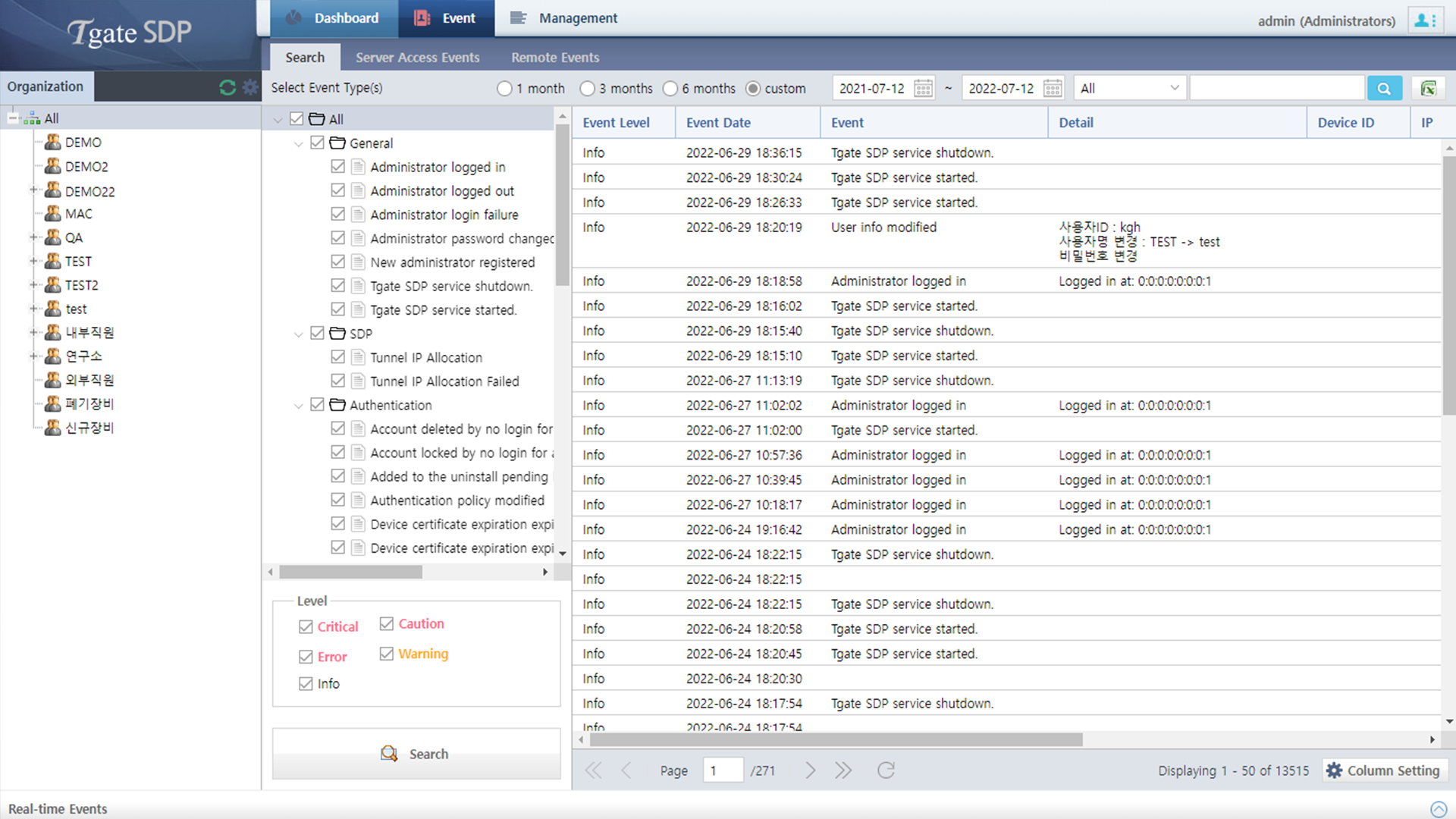
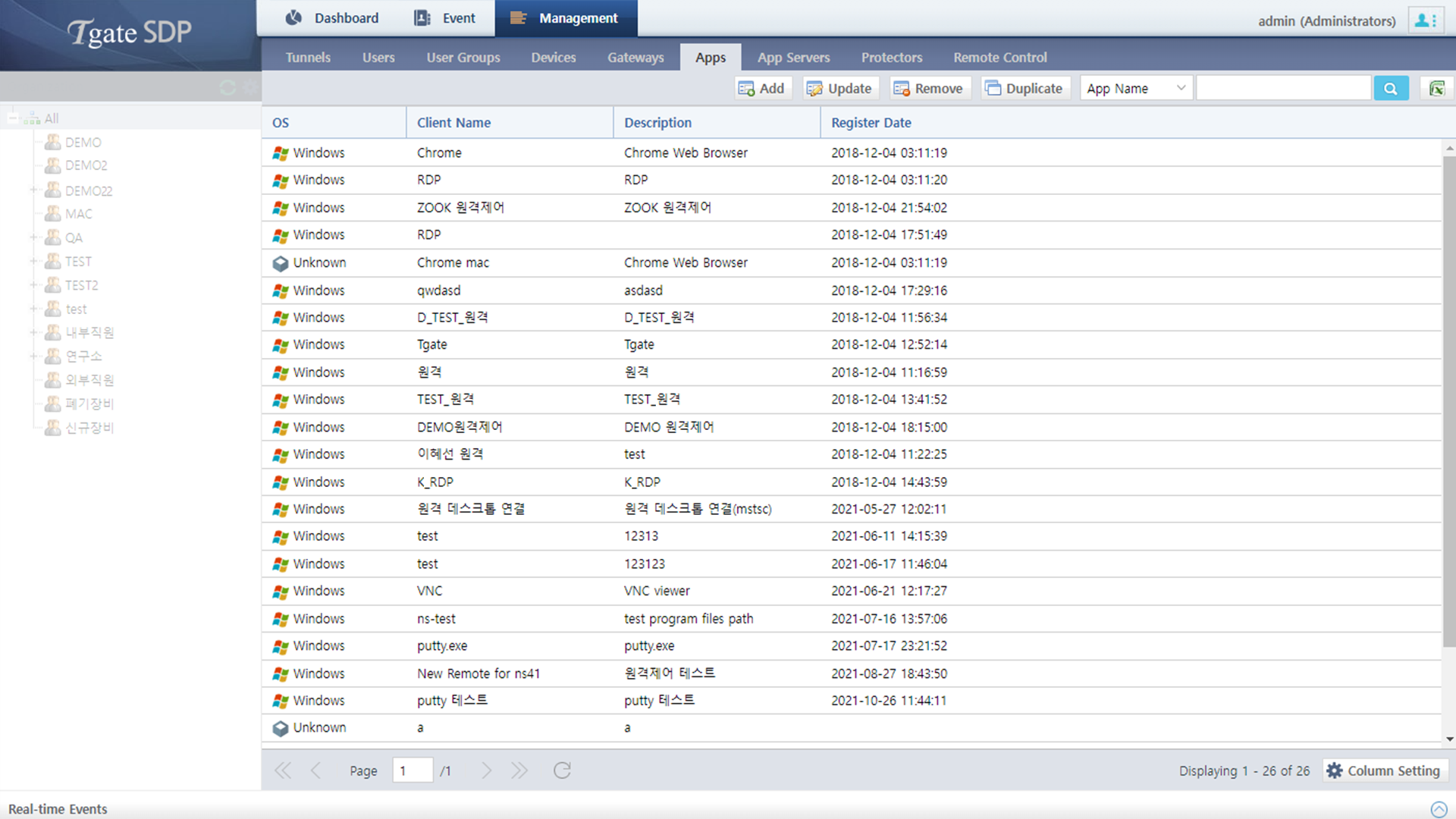
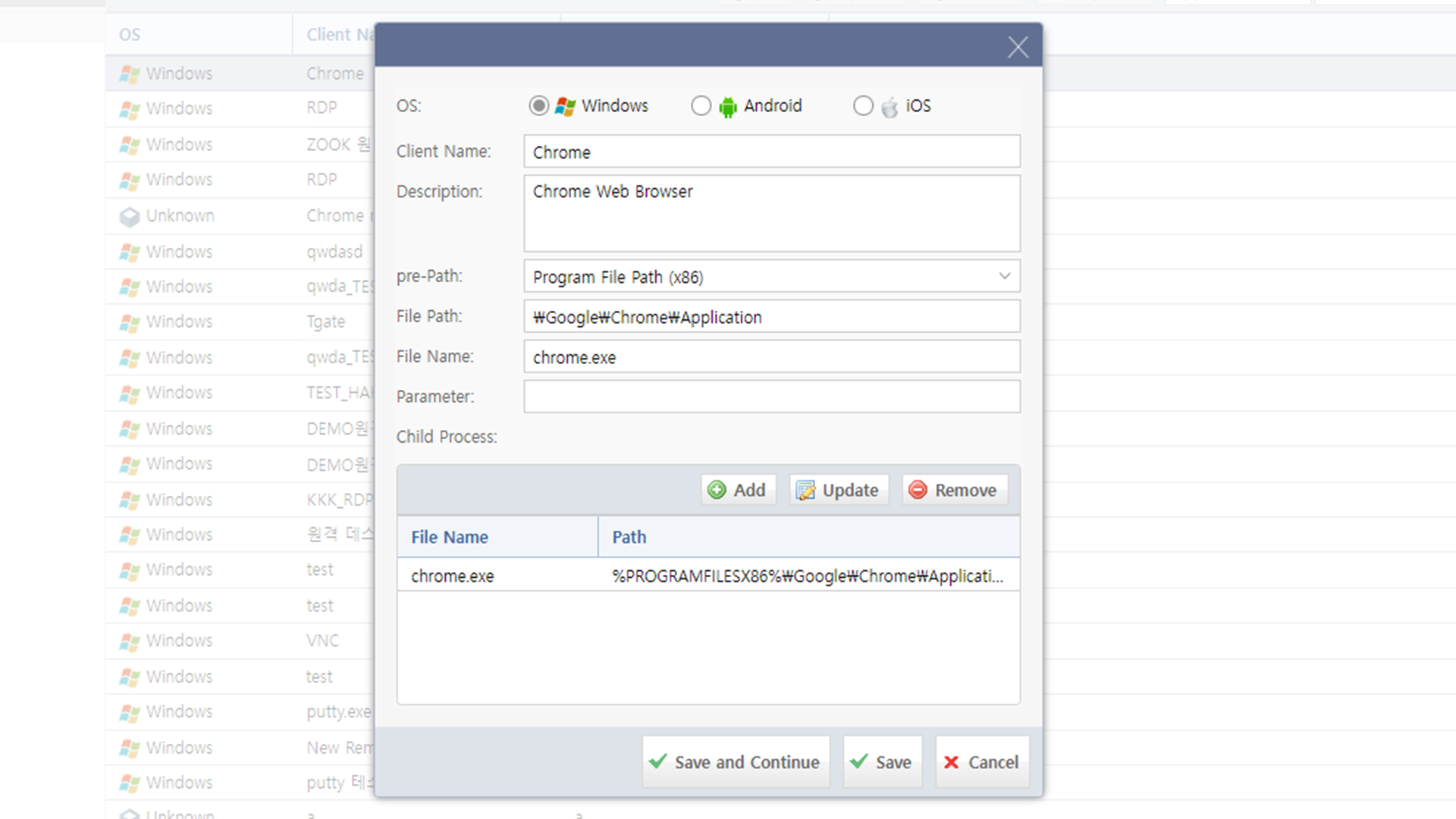
Screenshots
Main Features
Server Stealth
- Protects the gateway IP with a function that does not expose the target network information to the outside.
DDoS attack prevention
- By using SPA, reception is denied except for allowed packets.
* SPA : Single Packet Authorization
Dynamic Firewall
- Even if there is an access permission policy with a whitelist-based firewall, if there is no access for a certain period of time, it is changed to a blocked state.
- The access Permission/Block policy is changed according to the situation in real time.
App Binding
- It is possible to develop SDP-only applications using the SDK.
* SDK : Software Development Kit - According to the policy setting, only specified applications can use SDP communication.
IPsec Secure
- Provides a stable network with encrypted communication supported by the OS.
Access Authority Management
- Account and access rights management for device (HOTP) & user (RADIUS, Personnel DB linkage) authentication.
Strengths

Safely anywhere in the world

Now, the IoT is being realized in all areas and we are facing a highly productive environment. You can work much more efficiently than before, and you can dream of a more advanced future. But aren't you missing out on many opportunities due to security constraints?
Tgate SDP makes it possible to realize Zero Trust security anywhere in the world with strong security, ease of deployment and operation, and flexible scalability.
Benefits
Safely network
By hiding the network information of the service target, it is impossible to try hacking. This provides secure and reliable networking.
Freedom of workspace
You can do your business anywhere in the world and control IoT devices.
Significant cost savings
Dedicated lines are unnecessary, and the cost of adding a separate network infrastructure can be significantly reduced.
Infinite scalability
The limitations of workspace and network infrastructures that have been obstructed by the limitations of security are eliminated, and reaching more advanced business.
Time saving
Dramatically reduces the time it takes to set up the network environment by simply setting policies that connect users to the services they use.
Configuration

Gateway system requirements
| Division | Supported environment |
|---|---|
| OS | CentOS 7.6 |
| CPU | Dual Core 2.4 GHz |
| RAM | 4GB |
| HDD | 100GB |
| NIC | 2 |
| IP Address |
WAN section
LAN section
|